The high-severity CVE-2024-6387 in OpenSSH is a reintroduction of a 2006 flaw, and it allows unauthenticated RCE as root.
...moreSummary
Top Articles:
- OpenSea NFT Marketplace Faces Insider Hack
- Exposed Travis CI API Leaves All Free-Tier Users Open to Attack
- Patch Now: Cisco AnyConnect Bug Exploit Released in the Wild
- WordPress Plug-in Ninja Forms Issues Update for Critical Bug
- Adobe Issues Patch for Acrobat Zero-Day
- Multiple Windows, Adobe Zero-Days Anchor Knotweed Commercial Spyware
- Nissan Source Code Leaked via Misconfigured Git Server
- SolarWinds Attackers Gear Up for Typosquatting Attacks
- Google Discovers New Rowhammer Attack Technique
- 'Log in with...' Feature Allows Full Online Account Takeover for Millions
'RegreSSHion' Bug Threatens Takeover of Millions of Linux Systems

Published: 2024-07-01 19:38:55
Popularity: 25
Author: Tara Seals, Managing Editor, News, Dark Reading
🤖: "Linux takeover"
TeamViewer Credits Network Segmentation for Rebuffing APT29 Attack

Published: 2024-06-28 21:22:05
Popularity: 38
Author: Dark Reading Staff
🤖: "Network shields up"
Despite warnings from Health-ISAC and the NCC Group, the remote access software maker says defense-in-depth kept customers' data safe from Midnight Blizzard.
...moreGoogle Opens $250K Bug Bounty Contest for VM Hypervisor

Published: 2024-07-02 23:50:14
Popularity: None
Author: Dark Reading
🤖: "bug bounty party"
If security researchers can execute a guest-to-host attack using a zero-day vuln in the KVM open source hypervisor, Google will make it worth their while.
...moreThe Software Licensing Disease Infecting Our Nation's Cybersecurity

Published: 2024-06-18 14:00:00
Popularity: 10
Author: Steve Weber
🤖: ""Infection detected""
Forcing Microsoft to compete fairly is the most important next step in building a better defense against foreign actors.
...moreCritical VMware Bugs Open Swaths of VMs to RCE, Data Theft

Published: 2024-06-18 20:23:24
Popularity: 32
Author: Nate Nelson, Contributing Writer
🤖: ""VMware hacked""
A trio of bugs could allow hackers to escalate privileges and remotely execute code on virtual machines deployed across cloud environments.
...moreHijacking Scheme Takes Over High-Profile TikTok Accounts

Published: 2024-06-05 19:01:42
Popularity: 7
Author: Dark Reading Staff
🤖: "Hacked!"
Hijacking malware gets spread through TikTok's direct messaging and doesn't require the victim to click links or download anything.
...moreHotel Check-in Kiosks Expose Guest Data, Room Keys

Published: 2024-06-07 16:55:39
Popularity: 5
Author: Nathan Eddy, Contributing Writer
🤖: "data breach"
CVE-2024-37364 affects hospitality kiosks from Ariane Systems, which are used for self-check-in at more than 3,000 hotels worldwide.
...moreCritical Security Flaw Exposes 1 Million WordPress Sites to SQL Injection

Published: 2024-04-05 11:34:21
Popularity: None
Author: Elizabeth Montalbano, Contributing Writer
A researcher received a $5,500 bug bounty for discovering a vulnerability (CVE-2024-2879) in LayerSlider, a plug-in with more than a million active installations.
...more300K Internet Hosts at Risk for 'Devastating' Loop DoS Attack

Published: 2024-03-21 18:17:06
Popularity: 8
Author: Elizabeth Montalbano, Contributing Writer
Attackers can create a self-perpetuating, infinite scenario in such a way that volumes of traffic overwhelm network resources indefinitely.
...moreSession Takeover Bug in AWS Apache Airflow Reveals Larger Cloud Risk

Published: 2024-03-21 17:13:23
Popularity: 13
Author: Nate Nelson, Contributing Writer
A bug exposed users of an AWS workflow management service to cookie tossing, but behind the scenes lies an even deeper issue that runs across all of the top cloud services.
...moreAlabama Under DDoS Cyberattack by Russian-Backed Hacktivists

Published: 2024-03-14 19:43:25
Popularity: 125
Author: None
The hacktivist group Anonymous Sudan claims credit for a cyberattack that disrupted Alabama state government earlier this week.
...moreHow to Ensure Open Source Packages Are Not Landmines

Published: 2024-03-08 03:00:22
Popularity: None
Author: Agam Shah, Contributing Writer
CISA and OpenSSF jointly published new guidance recommending technical controls to make it harder for developers to bring malicious software components into code.
...moreRussia-Sponsored Cyberattackers Infiltrate Microsoft's Code Base

Published: 2024-03-08 17:22:50
Popularity: 45
Author: Tara Seals, Managing Editor, News, Dark Reading
The Midnight Blizzard APT is mounting a sustained, focused cyber campaign against the computing kahuna, using secrets it stole from emails back in January.
...moreStealth Bomber: Atlassian Confluence Exploits Drop Web Shells In-Memory

Published: 2024-03-10 13:13:39
Popularity: None
Author: Nathan Eddy, Contributing Writer
The proof-of-concept exploits for Atlassian Confluence would enable arbitrary code execution without requiring file system access.
...moreArmy Vet Spills National Secrets to Fake Ukrainian Girlfriend
Published: 2024-03-05 21:55:11
Popularity: 5
Author: Dark Reading Staff
The retired US Army lieutenant colonel faces up to 10 years in prison if convicted of sharing secret information about the Russia-Ukraine war with a scammer posing as romantic connection.
...more'VoltSchemer' Hack Allows Wireless Charger Takeovers

Published: 2024-02-21 21:46:12
Popularity: 183
Author: Dark Reading Staff
Researchers tested their theory on nine chargers, each different and available to consumers, and found them all vulnerable to their attacks.
...more'KeyTrap' DNS Bug Threatens Widespread Internet Outages

Published: 2024-02-20 18:16:24
Popularity: 92
Author: Becky Bracken, Editor, Dark Reading
Thanks to a 24-year-old security vulnerability tracked as CVE-2023-50387, attackers could stall DNS servers with just a single malicious packet, effectively taking out wide swaths of the Internet.
...moreJoomla XSS Bugs Open Millions of Websites to RCE

Published: 2024-02-20 21:38:03
Popularity: 21
Author: Dark Reading Staff
Improper content filtering in a core function allows multiple paths to exploitation for CVE-2024-21726.
...moreCISA Orders Ivanti VPN Appliances Disconnected: What to Do

Published: 2024-02-01 21:00:00
Popularity: 4
Author: Fahmida Y. Rashid, Managing Editor, Features, Dark Reading
US federal agencies have to disconnect, rebuild, and reconfigure all Ivanti Connect Secure and Policy Secure VPN appliances. This Tech Tip lists all the steps that need to happen.
...more'Commando Cat' Is Second Campaign of the Year Targeting Docker

Published: 2024-02-01 22:20:00
Popularity: 8
Author: Dark Reading Staff
The threat actor behind the campaign is still unknown, but it shares some similarities with other cyptojacking groups.
...moreCloudflare Falls Victim to Okta Breach, Atlassian Systems Cracked

Published: 2024-02-02 13:00:00
Popularity: 16
Author: Tara Seals, Managing Editor, News, Dark Reading
The cyberattackers, believed to be state sponsored, didn't get far into Cloudflare's global network, but not for lack of trying.
...moreGoogle Play Used to Spread 'Patchwork' APT's Espionage Apps

Published: 2024-02-02 15:23:33
Popularity: 7
Author: Becky Bracken, Editor, Dark Reading
The Indian state-sponsored cyberattackers lurked in Google's official app store, distributing a new RAT and spying on Pakistanis.
...moreSolarWinds Files Motion to Dismiss SEC Lawsuit

Published: 2024-01-29 21:38:00
Popularity: 7
Author: Becky Bracken, Editor, Dark Reading
Responding to SEC charges, SolarWinds fired back with a detailed defense of how a Russian-backed cyber espionage attack on its system was handled.
...moreThe CISO Role Undergoes a Major Evolution

Published: 2024-01-25 15:00:00
Popularity: 11
Author: Mark Bowling
Post-SolarWinds, it's no longer enough for chief information security officers to remain compliant and call it a day.
...moreGoogle Kubernetes Clusters Suffer Widespread Exposure to External Attackers

Published: 2024-01-25 16:40:00
Popularity: 16
Author: Elizabeth Montalbano, Contributing Writer
Misunderstanding the permissions of an authentication group in Google Kubernetes Engine (GKE) opens millions of containers to anyone with a Google account.
...moreChatGPT Cybercrime Discussions Spike to Nearly 3K Posts on Dark Web
Published: 2024-01-24 21:25:00
Popularity: 165
Author: Kristina Beek, Associate Editor, Dark Reading
And there were an additional 3,000 comments posted to the Dark Web about the sale of stolen ChatGPT accounts.
...moreNewly ID'ed Chinese APT Hides Backdoor in Software Updates

Published: 2024-01-26 21:00:00
Popularity: 9
Author: Nate Nelson, Contributing Writer
The threat actor went more than half a decade before being discovered — thanks to a remarkable backdoor delivered in invisible adversary-in-the-middle attacks.
...moreGlobal TeamCity Exploitation Opens Door to SolarWinds-Style Nightmare

Published: 2023-12-13 23:26:00
Popularity: 5
Author: Tara Seals, Managing Editor, News, Dark Reading
Russia's APT29 is going after a critical RCE flaw in the JetBrains TeamCity software developer platform, prompting governments worldwide to issue an urgent warning to patch.
...moreRussian Water Utility Hacked in Retaliation for Kyivstar Hit

Published: 2023-12-21 21:15:00
Popularity: 13
Author: Becky Bracken, Editor, Dark Reading
Moscow's Rosvodokanal water-management company was ransacked by Ukraine-aligned Blackjack group, with reports that the company's IT infrastructure was "destroyed."
...moreResearchers Use AI to Jailbreak ChatGPT, Other LLMs

Published: 2023-12-07 20:52:00
Popularity: 20
Author: None
"Tree of Attacks With Pruning" is the latest in a growing string of methods for eliciting unintended behavior from a large language model.
...moreRootkit Turns Kubernetes From Orchestration to Subversion

Published: 2023-11-22 16:15:25
Popularity: 22
Author: Robert Lemos, Contributing Writer, Dark Reading
Kubernetes compromises have usually led to attackers creating cryptomining containers, but the outcomes could be much worse, say researchers presenting at the Black Hat Europe conference.
...moreKinsing Cyberattackers Debut 'Looney Tunables' Cloud Exploits

Published: 2023-11-06 22:57:00
Popularity: 32
Author: Tara Seals, Managing Editor, News, Dark Reading
Admins need to patch immediately, as the prolific cybercrime group pivots from cryptomining to going after cloud secrets and credentials.
...moreSEC Charges Against SolarWinds CISO Send Shockwaves Through Security Ranks

Published: 2023-10-31 21:35:00
Popularity: 43
Author: Becky Bracken, Editor, Dark Reading
The legal actions may have a chilling effect on hiring CISOs, who are already in short supply, but may also expose just how budget-constrained most security executives are.
...morePatch Now: Massive RCE Campaign Wrangles Routers Into Botnet

Published: 2023-10-09 19:15:30
Popularity: 38
Author: Dark Reading Staff, Dark Reading
Thousands of devices, including D-Link and Zyxel gear, remain vulnerable to takeover despite the availability of patches for the several bugs being exploited by IZ1H9 campaign.
...more'Looney Tunables' Linux Flaw Sees Snowballing Proof-of-Concept Exploits

Published: 2023-10-09 20:00:00
Popularity: 40
Author: Nathan Eddy, Contributing Writer, Dark Reading
Following the publication of the critical Linux security vulnerability, security specialists released PoC exploits to test the implications of CVE-2023-4911.
...moreAdobe Acrobat Reader Vuln Now Under Attack

Published: 2023-10-11 18:15:00
Popularity: 32
Author: Dark Reading Staff, Dark Reading
CISA flags use-after-free bug now being exploited in the wild.
...moreMicrosoft Set to Retire Grunge-Era VBScript, to Cybercrime's Chagrin

Published: 2023-10-12 20:23:45
Popularity: 17
Author: Tara Seals, Managing Editor, News, Dark Reading
Popular malware like QakBot and DarkGate rely on VBScript, which dates back to 1996 — but their days are numbered now that Microsoft is finally deprecating the Windows programming language.
...moreSIM Card Ownership Slashed in Burkina Faso

Published: 2023-10-20 18:05:00
Popularity: 17
Author: Dark Reading Staff, Dark Reading
Users could hold up to five SIM cards previously, but now they can only have two; it's a move that the government says is intended to cut down mobile spam levels.
...moreVirtual Alarm: VMware Issues Major Security Advisory

Published: 2023-10-25 19:38:00
Popularity: 211
Author: Becky Bracken, Editor, Dark Reading
VMware vCenter Servers need immediate patch against critical RCE bug as race against threat actors begins.
...more'Log in with...' Feature Allows Full Online Account Takeover for Millions

Published: 2023-10-24 13:00:00
Popularity: 285
Author: Elizabeth Montalbano, Contributor, Dark Reading
Hundreds of millions of users of Grammarly, Vidio, and the Indonesian e-commerce giant Bukalapak are at risk for financial fraud and credential theft due to OAuth misfires — and other online services likely have the same problems.
...moreFake WinRAR PoC Exploit Conceals VenomRAT Malware

Published: 2023-09-26 15:23:51
Popularity: None
Author: Becky Bracken, Editor, Dark Reading
A supposed exploit for a notable RCE vulnerability in the popular Windows file-archiving utility delivers a big sting for unwitting researchers and cybercriminals.
...moreFake WinRAR PoC Exploit Conceals VenomRAT Malware

Published: 2023-09-20 20:09:00
Popularity: 52
Author: Tara Seals, Managing Editor, News, Dark Reading
A supposed exploit for a notable RCE vulnerability in the popular Windows file-archiving utility delivers a big sting for unwitting researchers and cybercriminals.
...moreYubico Goes Public

Published: 2023-09-20 22:00:00
Popularity: 2
Author: Dark Reading Staff, Dark Reading
The Swedish maker of Yubikeys has merged with special purpose acquisition company ACQ Bure.
...moreCisco Moves Into SIEM With $28B Deal to Acquire Splunk

Published: 2023-09-22 00:42:00
Popularity: 43
Author: Jeffrey Schwartz, Contributing Writer, Dark Reading
Cisco's surprise agreement could reshape secure information and event management (SIEM) and extended detection and response (XDR) markets.
...moreFake WinRAR PoC Exploit Conceals VenomRAT Malware

Published: 2023-09-26 12:37:49
Popularity: None
Author: Becky Bracken, Editor, Dark Reading
A supposed exploit for a notable RCE vulnerability in the popular Windows file-archiving utility delivers a big sting for unwitting researchers and cybercriminals.
...morePatch Now: Cisco AnyConnect Bug Exploit Released in the Wild

Published: 2023-06-22 15:53:52
Popularity: 4887
Author: Dark Reading Staff, Dark Reading
A ready-made, low-complexity path to pwning the popular enterprise VPN clients for remote workers is now circulating in the wild.
...moreGoogle Drive Deficiency Allows Attackers to Exfiltrate Workspace Data Without a Trace
Published: 2023-06-02 21:02:58
Popularity: None
Author: Contributor, Dark Reading
No activity logging in the free subscription for Google's Web-based productivity suite exposes enterprises to insider and other threats, researchers say.
...moreBilly Corgan Paid Off Hacker Who Threatened to Leak New Smashing Pumpkins Songs

Published: 2023-05-11 19:00:00
Popularity: 37
Author: Dark Reading Staff, Dark Reading
Corgan got FBI involved to track down the cybercriminal, who had stolen from other artists as well, he said.
...moreRebinding Attacks Persist With Spotty Browser Defenses

Published: 2023-05-17 18:21:29
Popularity: None
Author: Robert Lemos, Contributing Writer, Dark Reading
DNS rebinding attacks are not often seen in the wild, which is one reason why browser makers have taken a slower approach to adopting the web security standard.
...moreOnce Again, Malware Discovered Hidden in npm

Published: 2023-05-18 15:27:00
Popularity: 15
Author: Nathan Eddy, Contributing Writer, Dark Reading
Turkorat-poisoned packages sat in the npm development library for months, researchers say.
...moreMeta Hit With $1.3B Record-Breaking Fine for GDPR Violations

Published: 2023-05-22 19:29:00
Popularity: 32
Author: Dark Reading Staff, Dark Reading
The technology conglomerate has until later this year to end its transfer of European user's data across the Atlantic.
...morePyPI Shuts Down Over the Weekend, Says Incident Was Overblown

Published: 2023-05-22 20:52:00
Popularity: 45
Author: Nate Nelson, Contributing Writer, Dark Reading
The climate of concern around open source security and supply chain attacks may have caused a small story to become a big one.
...moreRed Hat Tackles Software Supply Chain Security

Published: 2023-05-25 21:50:00
Popularity: 93
Author: Jeffrey Schwartz, Contributing Writer, Dark Reading
The new Red Hat Trusted Software Supply Chain services help developers take a secure-by-design approach to build, deploy, and monitor software.
...moreTesla Whistleblower Leaks 100GB of Data, Revealing Safety Complaints

Published: 2023-05-26 17:32:00
Popularity: 28
Author: Dark Reading Staff, Dark Reading
Informants have released data that includes thousands of safety complaints the company has received about its self-driving capability, as well as sensitive information regarding current and past employees.
...moreSpotlight on 2023 Dan Kaminsky Fellow: Dr. Gus Andrews

Published: 2023-05-31 01:25:00
Popularity: 12
Author: Ericka Chickowski, Contributing Writer, Dark Reading
As the second Kaminsky Fellow, Andrews will study the use of threat intelligence to track campaigns against the human rights community.
...moreYet Another Toyota Cloud Data Breach Jeopardizes Thousands of Customers

Published: 2023-05-31 21:08:00
Popularity: 192
Author: Dark Reading Staff, Dark Reading
The newly found misconfigured cloud services are discovered just two weeks after an initial data breach affecting millions came to light.
...moreHuman-Assisted CAPTCHA-Cracking Services Supercharge Shopper Bots

Published: 2023-05-30 21:39:00
Popularity: 48
Author: Dark Reading Staff, Dark Reading
On-demand human solvers are now augmenting automated website cyberattacks, offering a better way around tougher anti-bot puzzles.
...moreGoogle Debuts Quality Ratings for Security Bug Disclosures

Published: 2023-05-19 13:05:00
Popularity: 34
Author: Becky Bracken, Editor, Dark Reading
New rules aim to level up the quality of submissions to Google and Android device Vulnerability Reward Program.
...moreTwitter 'Shadow Ban' Bug Gets Official CVE
Published: 2023-04-06 19:20:29
Popularity: 94
Author: Dark Reading Staff, Dark Reading
A flaw in Twitter code allows bot abuse to trick the algorithm into suppressing certain accounts.
...moreMicrosoft Patches 'Dangerous' RCE Flaw in Azure Cloud Service

Published: 2023-03-30 18:58:13
Popularity: 50
Author: Elizabeth Montalbano, Contributor, Dark Reading
The vulnerability would have allowed an unauthenticated attacker to execute code on a container hosted on one of the platform's nodes.
...moreGitHub's Private RSA SSH Key Mistakenly Exposed in Public Repository

Published: 2023-03-24 20:05:00
Popularity: 106
Author: Dark Reading Staff, Dark Reading
GitHub hastens to replace its RSA SSH host key after an exposure mishap threatens users with man-in-the-middle attacks and organization impersonation.
...moreNIST's Quantum-Proof Algorithm Has a Bug, Analysts Say

Published: 2023-03-08 17:36:54
Popularity: None
Author: Dark Reading
A team has found that the Crystals-Kyber encryption algorithm is open to side-channel attacks, under certain implementations.
...moreBooking.com's OAuth Implementation Allows Full Account Takeover

Published: 2023-03-02 16:16:00
Popularity: 15
Author: Elizabeth Montalbano, Contributor, Dark Reading
Researchers exploited issues in the authentication protocol to force an open redirection from the popular hotel reservations site when users used Facebook to log in to accounts.
...morePernicious Permissions: How Kubernetes Cryptomining Became an AWS Cloud Data Heist

Published: 2023-02-28 17:43:44
Popularity: 19
Author: Robert Lemos, Contributing Writer, Dark Reading
The opportunistic "SCARLETEEL" attack on a firm's Amazon Web Services account turns into targeted data theft after the intruder uses an overpermissioned service to jump into cloud system.
...moreFacebook Bug Allows 2FA Bypass Via Instagram

Published: 2023-01-30 19:00:00
Popularity: 67
Author: Dark Reading Staff, Dark Reading
The Instagram rate-limiting bug, found by a rookie hunter, could be exploited to bypass Facebook 2FA in vulnerable apps, researcher reports.
...moreDespite Breach, LastPass Demonstrates the Power of Password Management

Published: 2023-02-20 14:01:00
Popularity: 35
Author: Michael Bargury, CTO & Co-Founder, Zenity
What's scarier than keeping all of your passwords in one place and having that place raided by hackers? Maybe reusing insecure passwords.
...more87% of Container Images in Production Have Critical or High-Severity Vulnerabilities

Published: 2023-02-24 00:03:00
Popularity: 53
Author: Jeffrey Schwartz, Contributing Writer, Dark Reading
At the inaugural CloudNativeSecurityCon, DevSecOps practitioners discussed how to shore up the software supply chain.
...moreGoogle Fi Users Caught Up in T-Mobile Breach

Published: 2023-02-01 14:18:08
Popularity: 24
Author: Dark Reading Staff, Dark Reading
Google Fi mobile customers have been alerted that their SIM card serial numbers, phone numbers, and other data were exposed in T-Mobile hack.
...moreJailbreak Trick Breaks ChatGPT Content Safeguards

Published: 2023-02-08 22:05:00
Popularity: 66
Author: Dark Reading Staff, Dark Reading
Jailbreak command creates ChatGPT alter ego DAN, willing to create content outside of its own content restriction controls.
...moreGoTo Encrypted Backups Stolen in LastPass Breach

Published: 2023-01-26 02:45:40
Popularity: None
Author: Dark Reading
Encrypted backups for several GoTo remote work tools were exfiltrated from LastPass, along with encryption keys.
...moreHunting Insider Threats on the Dark Web

Published: 2023-01-23 15:00:00
Popularity: 143
Author: Jim Simpson, Director of Threat Intelligence, Searchlight Cyber
Use threat intelligence to reduce chance of success for malicious insider and Dark Web threats.
...moreJsonWebToken Security Bug Opens Servers to RCE

Published: 2023-01-09 17:45:00
Popularity: 147
Author: Nathan Eddy, Contributing Writer, Dark Reading
The JsonWebToken package plays a big role in the authentication and authorization functionality for many applications.
...moreGoogle WordPress Plug-in Bug Allows AWS Metadata Theft

Published: 2022-12-22 15:00:01
Popularity: 17
Author: Nathan Eddy, Contributing Writer, Dark Reading
A successful attacker could use the SSRF vulnerability to collect metadata from WordPress sites hosted on an AWS server, and potentially log in to a cloud instance to run commands.
...moreContainer Verification Bug Allows Malicious Images to Cloud Up Kubernetes

Published: 2022-12-23 18:18:27
Popularity: 29
Author: Tara Seals, Managing Editor, News, Dark Reading
A complete bypass of the Kyverno security mechanism for container image imports allows cyberattackers to completely take over a Kubernetes pod to steal data and inject malware.
...moreReport: Air-Gapped Networks Vulnerable to DNS Attacks

Published: 2022-12-08 14:12:04
Popularity: 119
Author: Elizabeth Montalbano, Contributor, Dark Reading
Common mistakes in network configuration can jeopardize the security of highly protected assets and allow attackers to steal critical data from the enterprise.
...moreKillnet Gloats About DDoS Attacks Downing Starlink, White House
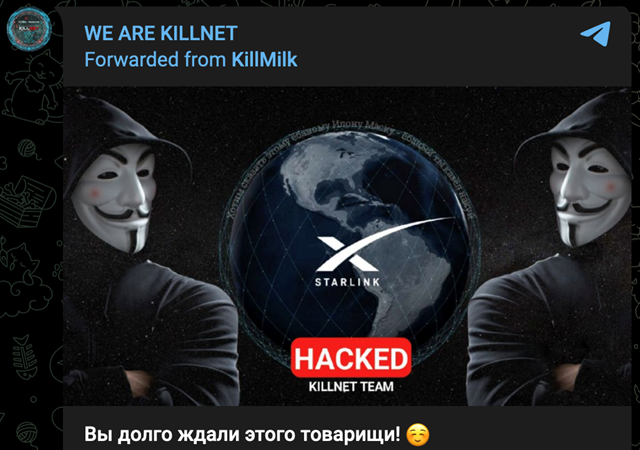
Published: 2022-11-29 18:15:00
Popularity: 40
Author: Becky Bracken, Editor, Dark Reading
Elon Musk-owned Starlink, WhiteHouse.gov, and the Prince of Wales were targeted by Killnet in apparent retaliation for its support of Ukraine.
...more$275M Fine for Meta After Facebook Data Scrape

Published: 2022-11-28 18:11:09
Popularity: 59
Author: Dark Reading Staff, Dark Reading
Meta has been found in violation of Europe's GDPR rules requiring the social media giant to protect user data by "design and default."
...moreIntel Processor UEFI Source Code Leaked

Published: 2022-10-11 17:49:46
Popularity: 66
Author: Dark Reading Staff, Dark Reading
Exposed code included private key for Intel Boot Guard, meaning it can no longer be trusted, according to a researcher.
...moreCritical Open Source vm2 Sandbox Escape Bug Affects Millions

Published: 2022-10-11 14:23:07
Popularity: 56
Author: Elizabeth Montalbano, Contributor, Dark Reading
Attackers could exploit the "Sandbreak" security bug, which has earned a 10 out of 10 on the CVSS scale, to execute a sandbox escape, achieve RCE, and run shell commands on a hosting machine.
...moreAndroid Leaks Wi-Fi Traffic Even When VPN Protection Features Are On

Published: 2022-10-12 16:20:35
Popularity: 14
Author: Elizabeth Montalbano, Contributor, Dark Reading
The platform lets network connectivity data escape outside of the secure tunnel when connected to a public network, posing a "privacy concern" for users with "certain threat models," researchers said.
...moreSignal to Ditch SMS/MMS Messaging on Android

Published: 2022-10-17 17:54:37
Popularity: 18
Author: Dark Reading Staff, Dark Reading
Main driver for the change: "Plaintext SMS messages are inherently insecure."
...moreIkea Smart Light System Flaw Lets Attackers Turn Bulbs on Full Blast

Published: 2022-10-05 20:00:00
Popularity: 59
Author: Dark Reading Staff, Dark Reading
With just one malformed Zigbee frame, attackers could take over certain Ikea smart lightbulbs, leaving users unable to turn the lights down.
...moreKey Takeaways From the Twitter Whistleblower's Testimony

Published: 2022-09-14 00:59:31
Popularity: 15
Author: Edge Editors, Dark Reading
Twitter did not know what data it had or who had access to it, Peiter "Mudge" Zatko told Congressional lawmakers during a Senate panel hearing.
...moreMalicious Apps With Millions of Downloads Found in Apple App Store, Google Play

Published: 2022-09-23 20:04:00
Popularity: 181
Author: Becky Bracken, Editor, Dark Reading
The ongoing ad fraud campaign can be traced back to 2019, but recently expanded into the iOS ecosystem, researchers say.
...moreSpell-Checking in Google Chrome, Microsoft Edge Browsers Leaks Passwords

Published: 2022-09-20 17:37:16
Popularity: 131
Author: Elizabeth Montalbano, Contributor, Dark Reading
It's called "spell-jacking": Both browsers have spell-check features that send data to Microsoft and Google when users fill out forms for websites or Web services.
...moreWhack-a-Mole: More Malicious PyPI Packages Spring Up Targeting Discord, Roblox

Published: 2022-08-16 18:51:56
Popularity: 19
Author: Dark Reading Staff, Dark Reading
Just as one crop of malware-laced software packages is taken down from the popular Python code repository, a new host arrives, looking to steal a raft of data.
...morePhishing Campaign Targets PyPI Users to Distribute Malicious Code

Published: 2022-08-30 14:16:23
Popularity: 35
Author: Elizabeth Montalbano, Contributor, Dark Reading
The first-of-its-kind campaign threatens to remove code packages if developers don’t submit their code to a "validation" process.
...moreMalicious Chrome Extensions Plague 1.4M Users
Published: 2022-08-30 20:00:00
Popularity: 19
Author: Dark Reading Staff, Dark Reading
Analysts find five cookie-stuffing extensions, including one that's Netflix-themed, that track victim browsing and insert rogue IDs into e-commerce sites to rack up fake affiliate payments.
...moreMultiple Windows, Adobe Zero-Days Anchor Knotweed Commercial Spyware

Published: 2022-07-27 18:49:47
Popularity: 950
Author: Tara Seals, Managing Editor, News, Dark Reading
Microsoft flagged the company's Subzero tool set as on offer to unscrupulous governments and shady business interests.
...moreWordPress Page Builder Plug-in Under Attack, Can't Be Patched

Published: 2022-07-18 17:55:01
Popularity: 29
Author: Dark Reading Staff, Dark Reading
An ongoing campaign is actively targeting the vulnerability in the Kaswara Modern WPBakery Page Builder Addon, which is still installed on up to 8,000 sites, security analysts warn.
...morePyPI Mandates 2FA, Plans Google Titan Key Giveaway

Published: 2022-07-12 22:42:37
Popularity: 23
Author: Dark Reading Staff, Dark Reading
Python's most popular package manager is intent on securing the supply chain by requiring developers to enable two-factor authentication.
...moreOpenSea NFT Marketplace Faces Insider Hack

Published: 2022-07-01 19:09:27
Popularity: 13817
Author: Becky Bracken, Editor, Dark Reading
OpenSea warns users that they are likely to be targeted in phishing attacks after a vendor employee accessed and downloaded its email list.
...moreCapital One Attacker Exploited Misconfigured AWS Databases

Published: 2022-06-20 21:25:39
Popularity: 25
Author: Tara Seals, Managing Editor, News, Dark Reading
After bragging in underground forums, the woman who stole 100 million credit applications from Capital One has been found guilty.
...moreWordPress Plug-in Ninja Forms Issues Update for Critical Bug

Published: 2022-06-17 18:53:38
Popularity: 4200
Author: Dark Reading Staff, Dark Reading
The code injection vulnerability is being actively exploited in the wild, researchers say.
...moreExposed Travis CI API Leaves All Free-Tier Users Open to Attack
Published: 2022-06-13 19:43:16
Popularity: 9178
Author: Dark Reading Staff, Dark Reading
Public Travis CI logs loaded with GitHub, AWS, Docker Hub account tokens, and other sensitive data could be leveraged for lateral cloud attacks.
...moreZero-Click Zoom Bug Allows Code Execution Just by Sending a Message
Published: 2022-05-25 19:21:04
Popularity: 36
Author: Tara Seals, Managing Editor, News, Dark Reading
Google has disclosed a nasty set of six bugs affecting Zoom chat that can be chained together for MitM and RCE attacks, no user interaction required.
...moreSolarWinds Attackers Gear Up for Typosquatting Attacks

Published: 2022-05-03 20:35:19
Popularity: 451
Author: Dark Reading Staff, Dark Reading
The same infrastructure traced back to Russian-speaking threat group Nobelium is being used to set up misspelled domain names, presaging impersonation attacks bent on credential harvesting, analysts say.
...moreHeroku: Cyberattacker Used Stolen OAuth Tokens to Steal Customer Account Credentials

Published: 2022-05-05 21:21:52
Popularity: 29
Author: Jai Vijayan, Contributing Writer
The same attack that allowed a threat actor to steal data from private Heroku GitHub repositories also resulted in the compromise of customer credentials, the company now says.
...moreDetails Released on SonicWall Flaws in SMA-100 Devices

Published: 2022-01-11 19:05:00
Popularity: 20
Author: Dark Reading Staff, Dark Reading
The most serious of the five vulnerabilities disclosed today can lead to unauthenticated remote code execution on affected devices.
...moreNew Firefox Sandbox Isolates Third-Party Libraries

Published: 2021-12-10 12:38:27
Popularity: 24
Author: Fahmida Y. Rashid, Features Editor, Dark Reading
RLBox can be used to protect web browsers and other software applications from vulnerabilities in subcomponents and libraries.
...moreResearcher Details Vulnerabilities Found in AWS API Gateway

Published: 2021-11-10 14:30:00
Popularity: 34
Author: Kelly Jackson Higgins, Executive Editor
AWS fixed the security flaws that left the API service at risk of so-called HTTP header-smuggling attacks, says the researcher who discovered them.
...moreMacOS Zero-Day Used in Watering-Hole Attacks

Published: 2021-11-15 22:23:23
Popularity: 27
Author: Robert Lemos, Contributing Writer
Attackers targeted Chinese pro-democracy groups using a vulnerability fixed in September along with a second vulnerability fixed early in the year, Google says.
...moreWhy Should I Care About HTTP Request Smuggling?
Published: 2021-09-29 15:26:23
Popularity: 17
Author: Asaf Karas, CTO. JFrog Security
HTTP request smuggling is a growing vulnerability, but you can manage the risk with proper server configuration.
...moreNSO Group Spyware Used On Journalists & Activists Worldwide

Published: 2021-07-19 18:53:00
Popularity: 28
Author: Dark Reading Staff
An investigation finds Pegasus spyware, intended for use on criminals and terrorists, has been used in targeted campaigns against others around the world.
...moreSophos Acquires Capsule8 for Linux Server & Container Security

Published: 2021-07-07 18:54:00
Popularity: 16
Author: Dark Reading Staff
The deal was announced the same day ZeroFox bought Dark Web intelligence firm Vigilante as a wave of security M&A continues.
...moreResearchers Learn From Nation-State Attackers' OpSec Mistakes

Published: 2021-07-06 21:42:00
Popularity: 19
Author: Kelly Sheridan Staff Editor, Dark Reading
NSA Funds Development & Release of D3FEND Framework

Published: 2021-06-22 17:26:00
Popularity: 18
Author: Dark Reading Staff
The framework, now available through MITRE, provides countermeasures to attacks.
...moreHigh-Level FIN7 Member Sentenced to 7 Years in Prison

Published: 2021-06-25 15:00:00
Popularity: 27
Author: Dark Reading Staff
Andrii Kolpakov, who served as a high-level pentester for the criminal group, was also ordered to pay $2.5 million in restitution.
...moreGoogle Launches SLSA, a New Framework for Supply Chain Integrity

Published: 2021-06-17 20:50:00
Popularity: 5
Author: Dark Reading Staff
The "Supply chain Levels for Software Artifacts" aims to ensure the integrity of components throughout the software supply chain.
...moreCritical Zero-Day Discovered in Fancy Product Designer WordPress Plug-in

Published: 2021-06-02 17:42:00
Popularity: 20
Author: Dark Reading Staff
The plug-in under active attack has been installed on more than 17,000 websites, say researchers.
...moreRussian Sentenced to 30 Months for Running Criminal Website

Published: 2021-05-25 18:32:00
Popularity: 21
Author: Dark Reading Staff
FBI says sales from illicit online shop deer.io exceeded $17 million
...moreGoogle Discovers New Rowhammer Attack Technique

Published: 2021-05-26 20:32:00
Popularity: 424
Author: Dark Reading Staff
Researchers publish the details of a new Rowhammer vulnerability called "Half-Double" that exploits increasingly smaller DRAM chips.
...moreAdobe Issues Patch for Acrobat Zero-Day

Published: 2021-05-11 21:02:00
Popularity: 3023
Author: Dark Reading Staff
The vulnerability is being exploited in limited attacks against Adobe Reader users on Windows.
...moreApple Issues Patches for Webkit Security Flaws

Published: 2021-05-04 21:21:00
Popularity: 34
Author: Dark Reading Staff
API Hole on Experian Partner Site Exposes Credit Scores

Published: 2021-04-29 19:49:00
Popularity: 78
Author: Dark Reading Staff
Student researcher is concerned security gap may exist on many other sites.
...moreNissan Source Code Leaked via Misconfigured Git Server

Published: 2021-01-06 22:00:00
Popularity: 583
Author: Dark Reading Staff
Leaked information includes source code of Nissan mobile apps, diagnostics tool, and market research tools and data, among other assets.
...moreT-Mobile Hacked -- Again

Published: 2021-01-04 19:10:00
Popularity: 151
Author: Dark Reading Staff
The wireless carrier has suffered a data breach for the fourth time since 2018.
...moreThe Coolest Hacks of 2020

Published: 2020-12-31 13:30:00
Popularity: 93
Author: Kelly Jackson Higgins Executive Editor at Dark Reading
Despite a pandemic and possibly the worst cyberattack campaign ever waged against the US, the year still had some bright spots when it came to "good" and creative hacks.
...moreFlash Dies but Warning Signs Persist: A Eulogy for Tech's Terrible Security Precedent

Published: 2020-12-04 15:00:00
Popularity: 68
Author: Rotem Iram Founder & CEO, At-Bay
Flash will be gone by the end of the year, but the ecosystem that allowed it to become a software security serial killer is ready to let it happen again.
...moreLaw Enforcement Disrupts VPN Services Enabling Cybercrime

Published: 2020-12-22 16:35:00
Popularity: 83
Author: Dark Reading Staff
The United States and international partners shut down three bulletproof hosting services used to facilitate criminal activity.
...moreCisco, Intel, Deloitte Among Victims of SolarWinds Breach: Report

Published: 2020-12-21 22:25:00
Popularity: 135
Author: Dark Reading Staff
The Wall Street Journal identified 24 businesses so far that have downloaded the SolarWinds software infected with malicious code.
...moreCollection of Metadata -- as Done by the NSA -- Likely Unconstitutional, US Court Suggests

Published: 2020-09-04 17:20:00
Popularity: 85
Author: Robert Lemos Contributing Writer
A ruling in an appeal by four men convicted of material support for terrorism finds that the National Security Agency's metadata collection program not only violated the prevailing law at the time but was also likely unconstitutional.
...moreWordPress Plug-in Has Critical Zero-Day

Published: 2020-09-08 19:00:00
Popularity: 95
Author: Dark Reading Staff
The vulnerability in WordPress File Manager could allow a malicious actor to take over the victim's website.
...moreREvil Ransomware Hits Jack Daniel's Manufacturer

Published: 2020-08-17 18:00:00
Popularity: 268
Author: Dark Reading Staff
Attackers who targeted US spirits manufacturer Brown-Forman reportedly stole a terabyte of confidential data.
...more70,000+ WordPress Sites Affected by Critical Plug-in Flaw

Published: 2020-07-29 19:10:00
Popularity: 110
Author: Dark Reading Staff
A vulnerability in the wpDiscuz plug-in could let attackers remotely execute code on the servers of affected websites.
...moreCouchSurfing Investigates Potential Data Breach

Published: 2020-07-23 17:15:00
Popularity: 23
Author: Dark Reading Staff
The service has reportedly hired a security firm after 17 million user records were found on a public hacking forum.
...moreAdobe Releases PDF Protected Mode for Acrobat DC

Published: 2020-06-16 20:45:00
Popularity: 12
Author: Dark Reading Staff
The preview, open to Windows users, opens PDF files in a sandbox to protect users who open malicious Acrobat documents.
...moreZoom Changes Course on End-to-End Encryption

Published: 2020-06-17 21:40:00
Popularity: 101
Author: Dark Reading Staff
The videoconferencing company now says it will offer end-to-end encryption to all users beginning in July.
...moreAdobe Releases PDF Protected Mode for Document Cloud

Published: 2020-06-16 20:45:00
Popularity: 69
Author: Dark Reading Staff
The preview, open to Windows users, opens PDF files in a sandbox to protect users who open malicious Acrobat documents.
...moreFake COVID-19 Contact-Tracing Apps Infect Android Phones

Published: 2020-06-10 17:45:00
Popularity: 183
Author: Dark Reading Staff
Researchers find 12 Android applications disguised as official COVID-19 contact tracing apps installing malware onto devices.
...moreRare NSA Advisory About Russia-Based Cyberattacks Unlikely to Stop Them

Published: 2020-06-01 17:35:00
Popularity: 189
Author: Robert Lemos Contributing Writer
The Sandworm group -- behind disinformation and election-hacking campaigns and responsible for a 2016 power outage in the Ukraine -- is now targeting e-mail servers.
...moreNSA Warns Russia's 'Sandworm' Group Is Targeting Email Servers

Published: 2020-05-28 18:15:00
Popularity: 114
Author: Dark Reading Staff
The Russian military group has been exploiting a flaw in the Exim mail transfer agent since last August, the NSA reports.
...moreZoom Acquires Keybase, Plans for End-to-End Encrypted Chats

Published: 2020-05-07 16:15:00
Popularity: 73
Author: Dark Reading Staff
The company's first acquisition to date is part of a 90-day plan to improve security in its video communications platform.
...moreResearchers Find Vulnerabilities in Popular Remote Learning Plug-ins

Published: 2020-04-30 16:00:00
Popularity: 94
Author: Robert Lemos Contributing Writer
As more students move to online learning platforms, vulnerability researchers are revealing security flaws in some common software plug-ins.
...moreHealth Prognosis on the Security of IoMT Devices? Not Good

Published: 2020-04-25 13:30:00
Popularity: 142
Author: Nicole Ferraro Freelance Writer
As more so-called Internet of Medical Things devices go online, hospitals and medical facilities face significant challenges in securing them from attacks that could endanger patients' lives.
...moreMozilla Patches Two Critical Zero-Days in Firefox

Published: 2020-04-06 15:45:00
Popularity: 103
Author: Dark Reading Staff
The latest release of Firefox brings fixes for two Critical vulnerabilities already seen exploited in the wild.
...moreProof of Concept Released for kr00k Wi-Fi Vulnerability

Published: 2020-03-20 16:45:00
Popularity: 90
Author: Dark Reading Staff
The code demonstrates a relatively simple method to exploit a vulnerability in more than a billion devices.
...moreGoogle Adds More Security Features Via Chronicle Division

Published: 2020-02-25 18:30:00
Popularity: 48
Author: Robert Lemos Contributing Writer
Order out of chaos? The saga of Chronicle continues with new security features for the Google Cloud Platform.
...moreKr00k Wi-Fi Vulnerability Affected a Billion Devices

Published: 2020-02-26 15:15:00
Popularity: 276
Author: Robert Lemos Contributing Writer
Routers and devices with Broadcom and Cypress Wi-Fi chipsets could be forced to sometimes use encryption keys consisting of all zeroes. Now patched, the issue affected a billion devices, including those from Amazon, Apple, Google, and Samsung.
...moreTesla, SpaceX Parts Manufacturer Suffers Data Breach

Published: 2020-03-02 17:45:00
Popularity: 265
Author: Dark Reading Staff
Visser Precision has confirmed a security incident likely caused by the data-stealing DoppelPaymer ransomware.
...moreClearview AI Customers Exposed in Data Breach

Published: 2020-02-28 01:00:00
Popularity: 170
Author: Dark Reading Staff
Customers for the controversial facial recognition company were detailed in a log file leaked to news organizations.
...moreKubernetes Shows Built-in Weakness

Published: 2020-02-04 15:45:00
Popularity: 75
Author: Curtis Franklin Jr. Senior Editor at Dark Reading
🤖: ""Security hole""
A Shmoocon presentation points out several weaknesses built in to Kubernetes configurations and how a researcher can exploit them.
...moreUnited Nations Data Breach Started with Microsoft SharePoint Bug

Published: 2020-01-30 18:10:00
Popularity: 138
Author: Dark Reading Staff
A remote code execution flaw enabled a breach of UN offices in Geneva and Vienna, as well as the Office of the High Commissioner for Human Rights.
...moreNFL, Multiple NFL Teams' Twitter Accounts Hacked and Hijacked

Published: 2020-01-29 00:30:00
Popularity: 134
Author: Dark Reading Staff
Hackers claiming to be from the hacktivist group OurMine temporarily took over Twitter accounts of the NFL and several teams in the league.
...more'CardPlanet' Operator Pleads Guilty in Federal Court

Published: 2020-01-24 21:30:00
Popularity: 128
Author: Dark Reading Staff
Russian national faced multiple charges in connection with operating the marketplace for stolen credit-card credentials, and a forum for VIP criminals to offer their services.
...moreMalicious Google Play Apps Linked to SideWinder APT

Published: 2020-01-06 22:20:00
Popularity: 134
Author: Kelly Sheridan Staff Editor, Dark Reading
The active attack involving three malicious Android applications is the first exploiting CVE-2019-2215, Trend Micro researchers report.
...moreLas Vegas Suffers Cyberattack on First Day of CES

Published: 2020-01-09 01:45:00
Popularity: 205
Author: Dark Reading Staff
The attack, still under investigation, hit early in the morning of Jan. 7.
...moreSiemens Contractor Sentenced for Writing 'Logic Bombs'

Published: 2019-12-17 16:40:00
Popularity: 92
Author: Dark Reading Staff
David Tinley, 62, rigged software he wrote for the company starting in 2014 and into 2016, causing the programs to fail.
...moreData Leak Week: Billions of Sensitive Files Exposed Online

Published: 2019-12-10 23:30:00
Popularity: 156
Author: Kelly Jackson Higgins Executive Editor at Dark Reading
A total of 2.7 billion email addresses, 1 billion email account passwords, and nearly 800,000 applications for copies of birth certificate were found on unsecured cloud buckets.
...moreBlink Cameras Found with Multiple Vulnerabilities

Published: 2019-12-10 20:50:00
Popularity: 70
Author: Dark Reading Staff
Researchers found three broad types of vulnerabilities, one of which should be particularly concerning to consumers.
...moreMicrosoft Fixes Windows Zero-Day on Lightest Patch Tuesday of 2019

Published: 2019-12-10 21:30:00
Popularity: 74
Author: Kelly Sheridan Staff Editor, Dark Reading
This month's batch of security updates addresses 36 CVEs, seven of which are rated Critical and one of which has been exploited in the wild.
...moreAttackers Continue to Exploit Outlook Home Page Flaw

Published: 2019-12-04 15:45:00
Popularity: 53
Author: Robert Lemos Contributing Writer
Cisco Webex & Zoom Bug Lets Attackers Spy on Conference Calls

Published: 2019-10-01 21:10:00
Popularity: 158
Author: Kelly Sheridan Staff Editor, Dark Reading
The "Prying-Eye" vulnerability could let intruders scan for unprotected meeting IDs and snoop on conference calls.
...moreNSA Issues Advisory on VPN Vulnerability Trio

Published: 2019-10-08 20:55:00
Popularity: 219
Author: Dark Reading Staff
Vulnerabilities with Pulse Secure, Fortinet, and Palo Alto Networks VPNs are called out in the advisory.
...more218M Words with Friends Players Compromised in Data Breach

Published: 2019-09-30 15:00:00
Popularity: 285
Author: Dark Reading Staff
The same attacker was reportedly behind the Collection #1 and Collection #2 data dumps earlier this year.
...moreDoorDash Breach Affects 4.9M Merchants, Customers, Workers

Published: 2019-09-27 14:30:00
Popularity: 145
Author: Dark Reading Staff
The May 4 incident exposed data belonging to users on the platform on or before April 5, 2018.
...moreData Leak Affects Most of Ecuador's Population

Published: 2019-09-16 17:40:00
Popularity: 69
Author: Kelly Sheridan Staff Editor, Dark Reading
An unsecured database containing 18GB of data exposed more than 20 million records, most of which held details about Ecuadorian citizens.
...moreCourt Rules In Favor of Firm 'Scraping' Public Data

Published: 2019-09-16 18:00:00
Popularity: 76
Author: Dark Reading Staff
US appeals court said a company can legally use publicly available LinkedIn account information.
...moreVMware to Buy Carbon Black for $2.1B

Published: 2019-08-23 15:30:00
Popularity: 70
Author: Dark Reading Staff
Virtual machine giant's big cloud move includes plans to shell out $2.7 billion in stock transactions for Pivotal Software.
...moreImperva Customer Database Exposed

Published: 2019-08-27 21:00:00
Popularity: 110
Author: Dark Reading Staff
A subset of customers for the company's Incapsula web application firewall had their email addresses, hashed/salted passwords, and more open to unauthorized access, Imperva announced.
...moreSecurity Flaws Discovered in 40 Microsoft-Certified Device Drivers

Published: 2019-08-12 21:30:00
Popularity: 131
Author: Curtis Franklin Jr. Senior Editor at Dark Reading
🤖: ""Driver fail""
Attackers can use vulnerable drivers to escalate privilege and execute malicious code in every part of the system.
...more700K Guest Records Stolen in Choice Hotels Breach

Published: 2019-08-13 16:20:00
Popularity: 163
Author: Dark Reading Staff
Cybercriminals reportedly stole the information from an exposed MongoDB database on a third-party server.
...moreBioStar 2 Leak Exposes 23GB Data, 1M Fingerprints

Published: 2019-08-14 15:30:00
Popularity: 177
Author: Dark Reading Staff
Thousands of organizations, including banks, governments, and the UK Metropolitan Police, use the biometric security tool to authenticate users.
...moreMalware Researcher Hutchins Sentenced to Supervised Release

Published: 2019-07-26 19:10:00
Popularity: 141
Author: Dark Reading Staff
Marcus Hutchins, the researcher known for stopping WannaCry, avoids jail time over charges of creating and distributing Kronos malware.
...moreMalware in PyPI Code Shows Supply Chain Risks

Published: 2019-07-19 17:30:00
Popularity: 164
Author: Curtis Franklin Jr. Senior Editor at Dark Reading
🤖: ""Python Pandemonium""
A code backdoor in a package on the Python Package Index demonstrates the importance of verifying code brought in from code repositories.
...moreLenovo NAS Firmware Flaw Exposes Stored Data

Published: 2019-07-16 21:20:00
Popularity: 192
Author: Jai Vijayan Contributing Writer
More than 5,100 vulnerable devices containing multiple terabytes of data are open to exploitation, researchers found.
...moreVulnerability Found in GE Anesthesia Machines

Published: 2019-07-10 17:30:00
Popularity: 92
Author: Dark Reading Staff
GE Healthcare has released a statement claiming the bug is not in the machine itself and does not pose direct risk to patients.
...moreD-Link Agrees to Strengthen Device Security

Published: 2019-07-04 03:30:00
Popularity: 186
Author: Dark Reading Staff
A settlement with the FTC should mean comprehensive security upgrades for D-Link routers and IP camera.
...moreHow Hackers Infiltrate Open Source Projects

Published: 2019-06-27 18:45:00
Popularity: 183
Author: Curtis Franklin Jr. Senior Editor at Dark Reading
The dependency trees of modern software-development make smaller open-source projects vulnerable to hackers sabotaging code.
...moreChronicle Folds into Google

Published: 2019-06-27 22:30:00
Popularity: 73
Author: Curtis Franklin Jr. Senior Editor at Dark Reading
🤖: ""Newspaper disappears""
Alphabet's enterprise cybersecurity division will become part of the Google security portfolio.
...moreCloud Provider PCM Suffers Data Breach

Published: 2019-06-28 15:40:00
Popularity: 218
Author: Dark Reading Staff
Attackers were reportedly able to compromise email and file-sharing systems for some of PCM's customers.
...morePatch Now: Another Google Zero-Day Under Exploit in the Wild

Published: 2024-05-16 12:48:06
Popularity: 15
Author: Dark Reading Staff
Google has rolled an emergency patch for CVE-2024-4947, the third Chrome zero-day it's addressed in the past week.
...moreSEC Adds New Incident Response Rules for Financial Sector
Published: 2024-05-17 18:03:51
Popularity: 8
Author: Dark Reading Staff
Financial firms covered under new regulations will be required to establish a clear response and communications plan for customer data breaches.
...moreMicrosoft Has Yet to Patch 7 Pwn2Own Zero-Days

Published: 2024-05-17 12:00:00
Popularity: 63
Author: Nate Nelson, Contributing Writer
A number of serious Windows bugs still haven't made their way into criminal circles, but that won't remain the case forever — and time is running short before ZDI releases exploit details.
...moreD-Link Routers Vulnerable to Takeover Via Exploit for Zero-Day

Published: 2024-05-15 15:42:28
Popularity: 10
Author: Elizabeth Montalbano, Contributing Writer
A vulnerability in the HNAP login request protocol that affects a family of devices gives unauthenticated users root access for command execution.
...moreMicrosoft Will Hold Executives Accountable for Cybersecurity

Published: 2024-05-08 13:00:00
Popularity: 54
Author: Jai Vijayan, Contributing Writer
At least a portion of executive compensation going forward will be tied to meeting security goals and metrics.
...moreIs CISA's Secure by Design Pledge Toothless?

Published: 2024-05-10 18:21:29
Popularity: 9
Author: Nate Nelson, Contributing Writer
CISA's agreement is voluntary and, frankly, basic. Signatories say that's a good thing.
...moreRussia's Fancy Bear Pummels Windows Print Spooler Bug

Published: 2024-04-23 13:21:39
Popularity: 14
Author: Elizabeth Montalbano, Contributing Writer
The infamous Russian threat actor has created a custom tool called GooseEgg to exploit CVE-2022-38028 in cyber-espionage attacks against targets in Ukraine, Western Europe, and North America.
...moreCisco Zero-Days Anchor 'ArcaneDoor' Cyber-Espionage Campaign

Published: 2024-04-25 15:59:45
Popularity: 6
Author: Elizabeth Montalbano, Contributing Writer
Attacks by a previously unknown threat actor leveraged two bugs in firewall devices to install custom backdoors on several government networks globally.
...moreCritical Bug Allows DoS, RCE, Data Leaks in All Major Cloud Platforms

Published: 2024-05-20 19:31:25
Popularity: 95
Author: Nate Nelson, Contributing Writer
An on-by-default endpoint in ubiquitous logging service Fluent Bit contains an oversight that hackers can toy with to rattle most any cloud environment.
...moreOkta Warns Once Again of Credential-Stuffing Attacks

Published: 2024-05-30 15:43:41
Popularity: 6
Author: Elizabeth Montalbano, Contributing Writer
🤖: "password fail"
This time it's the identity management service provider's cross-origin authentication feature that's being targeted by adversaries.
...moreStudents Spot Washing Machine App Flaw That Gives Out Free Cycles

Published: 2024-05-20 19:03:41
Popularity: 28
Author: Kristina Beek, Associate Editor, Dark Reading
🤖: "Spin Cycle"
UCSC students say that after reporting the bug months ago, they're still able to rack up unlimited free wash loads at their local laundromat.
...moreGoogle Opens $250K Bug Bounty Contest for VM Hypervisor

Published: 2024-07-01 20:35:22
Popularity: 12
Author: Dark Reading Staff
🤖: "Bug Bounty Party"
If security researchers can execute a guest-to-host attack using a zero-day vulnerability in the KVM open source hypervisor, Google will make it worth their while.
...moreSnowflake Account Attacks Driven by Exposed Legitimate Credentials

Published: 2024-07-17 14:00:00
Popularity: 18
Author: Stephanie Schneider
🤖: "passwords gone wild"
Credential management gets a boost with the latest infostealers' extortion campaign built on info stolen from cloud storage systems.
...more20 Million Trusted Domains Vulnerable to Email Hosting Exploits

Published: 2024-07-18 17:53:43
Popularity: 21
Author: Elizabeth Montalbano, Contributing Writer
🤖: "Email fail"
Three newly discovered SMTP smuggling attack techniques can exploit misconfigurations and design decisions made by at least 50 email-hosting providers.
...moreUS Data Breach Victim Numbers Increase by 1,000%, Literally

Published: 2024-07-18 21:04:59
Popularity: 14
Author: Dark Reading Staff
🤖: ""Data Alert!""
Though the number of victims has risen, the actual number of breaches has gone down, as fewer, bigger breaches affect more individuals.
...moreSizable Chunk of SEC Charges Against SolarWinds Tossed Out of Court

Published: 2024-07-18 21:43:20
Popularity: 7
Author: Becky Bracken, Senior Editor, Dark Reading
🤖: ""Solar Flare Up""
Judge dismisses claims against SolarWinds for actions taken after its systems had been breached, but allows the case to proceed for alleged misstatements prior to the incident.
...moreSwipe Right for Data Leaks: Dating Apps Expose Location, More

Published: 2024-07-22 18:18:55
Popularity: 145
Author: Elizabeth Montalbano, Contributing Writer
🤖: "Data leak alert"
Apps like Tinder, Bumble, Grindr, Badoo, OKCupid, MeetMe, and Hinge all have API vulnerabilities that expose sensitive user data, and six allow a threat actor to pinpoint exactly where someone is.
...moreCloud Security Alliance Introduces Certificate of Cloud Security Knowledge

Published: 2024-07-22 20:29:12
Popularity: 6
Author: None
🤖: "Cloudy with a chance of breach"
Wanted: An SBOM Standard to Rule Them All

Published: 2024-07-23 14:00:00
Popularity: 8
Author: Eric Braun
🤖: "Software security chaos"
A unified standard is essential for realizing the full potential of SBOMs in enhancing software supply chain security.
...moreAttackers Exploit 'EvilVideo' Telegram Zero-Day to Hide Malware

Published: 2024-07-23 16:21:16
Popularity: 7
Author: Elizabeth Montalbano, Contributing Writer
🤖: "Sneaky malware"
An exploit sold on an underground forum requires user action to download an unspecified malicious payload.
...moreGoodbye? Attackers Can Bypass 'Windows Hello' Strong Authentication

Published: 2024-07-23 19:16:12
Popularity: 41
Author: Jeffrey Schwartz, Contributing Writer
🤖: "windows hello fail"
Accenture researcher undercut WHfB's default authentication using open source Evilginx adversary-in-the-middle (AitM) reverse-proxy attack framework.
...moreCrowdStrike Outage Losses Estimated at a Staggering $5.4B

Published: 2024-07-26 20:36:57
Popularity: 7
Author: Dark Reading Staff
🤖: "System down 💻"
Researchers track the healthcare sector as experiencing the biggest financial losses, with banking and transportation following close behind.
...moreSecurity Firm Accidentally Hires North Korean Hacker, Did Not KnowBe4

Published: 2024-07-25 15:32:05
Popularity: 22
Author: Elizabeth Montalbano, Contributing Writer
🤖: "oops, hired wrong guy"
A software engineer hired for an internal IT AI team immediately became an insider threat by loading malware onto his workstation.
...moreCrowdStrike 'Updates' Deliver Malware & More as Attacks Snowball

Published: 2024-07-25 20:51:01
Popularity: 43
Author: Nate Nelson, Contributing Writer
🤖: "Malware Alert"
The fake updates are part of a phishing and fraud surge that is both more voluminous and more targeted that the usual activity around national news stories.
...moreCritical, Actively Exploited Jenkins RCE Bug Suffers Patch Lag

Published: 2024-08-22 19:42:04
Popularity: None
Author: Nate Nelson, Contributing Writer
🤖: ""Exploit alert""
A 7-month-old bug in an OSS CI/CD server is still being actively exploited, thanks to spotty patching, CISA warns.
...moreGitHub Attack Vector Cracks Open Google, Microsoft, AWS Projects

Published: 2024-08-14 14:16:57
Popularity: 22
Author: Elizabeth Montalbano, Contributing Writer
🤖: ""Ouch, they're vulnerable""
Cloud services and thus millions of end users who access them could have been affected by the poisoning of artifacts in the development workflow of open source projects.
...moreDNC Credentials Compromised by 'IntelFetch' Telegram Bot

Published: 2024-08-14 10:00:00
Popularity: 11
Author: Nathan Eddy, Contributing Writer
🤖: "Hacked again"
The Democratic National Convention soon to take place in Chicago, already under heavy security, faces an additional threat in the form of stolen credentials for delegates.
...moreCritical AWS Vulnerabilities Allow S3 Attack Bonanza

Published: 2024-08-08 12:00:00
Popularity: 20
Author: Jeffrey Schwartz, Contributing Writer
🤖: "Cloud chaos"
Researchers at Aqua Security discovered the "Shadow Resource" attack vector and the "Bucket Monopoly" problem, where threat actors can guess the name of S3 buckets based on their public account IDs.
...moreMemory Safety Is Key to Preventing Hardware Hacks

Published: 2024-08-08 22:33:36
Popularity: 4
Author: Agam Shah, Contributing Writer
🤖: ""Secure Your RAM""
Spectre and Meltdown exposed just how easy a target computer memory was for attackers. Several efforts are underway to protect memory.
...moreCCTV Zero-Day Exposes Critical Infrastructure to Mirai Botnet

Published: 2024-08-28 21:00:08
Popularity: 9
Author: Becky Bracken, Senior Editor, Dark Reading
🤖: ""Surveillance breached""
CISA warned about the RCE zero-day vulnerability in AVTECH IP cameras in early August, and now vulnerable systems are being used to spread malware.
...moreBiden Admin Files Charges Against Election Meddlers From Russia

Published: 2024-09-05 19:39:53
Popularity: 5
Author: Kristina Beek, Associate Editor, Dark Reading
🤖: "Russian hackers caught"
Working with the Treasury and Justice departments, the president has sanctioned anti-democratic Russian adversaries.
...moreUsing Transparency & Sharing to Defend Critical Infrastructure

Published: 2024-09-06 14:00:00
Popularity: 6
Author: Travis Galloway
🤖: "#ShieldUp"
No organization can single-handedly defend against sophisticated attacks. Governments and private sector entities need to collaborate, share information, and develop defenses against cyber threats
...moreZero-Click MediaTek Bug Opens Phones, Wi-Fi to Takeover

Published: 2024-09-21 20:29:58
Popularity: None
Author: Dark Reading
🤖: ""Wi-Fi hack""
Critical-rated CVE-2024-20017 allows remote code execution (RCE) on a range of phones and Wi-Fi access points from a variety of OEMs.
...moreAir-Gapped Networks Vulnerable to Acoustic Attack via LCD Screens

Published: 2024-09-11 13:00:44
Popularity: 62
Author: Nate Nelson, Contributing Writer
🤖: ""Eavesdropping in silence""
In the "PixHell" attack, sound waves generated by pixels on a screen can transmit information across seemingly impenetrable air gaps.
...moreWiz Launches Wiz Code Application Security Tool

Published: 2024-09-10 21:47:40
Popularity: 4
Author: Jennifer Lawinski, Contributing Writer
🤖: "Code cracker 🕷️💻"
Wiz Code identifies and flags cloud risks in code to help improve collaboration between security and development teams.
...morePython-Based Malware Slithers Into Systems via Legit VS Code

Published: 2024-10-02 15:18:01
Popularity: 6
Author: Elizabeth Montalbano, Contributing Writer
🤖: "Sneaky snake"
The prolific Chinese APT Mustang Panda is the likely culprit behind a sophisticated cyber-espionage attack that sets up persistent remote access to victim machines.
...moreIvanti Cloud Bug Goes Under Exploit After Alarms Are Raised

Published: 2024-09-16 21:04:22
Popularity: 8
Author: Dark Reading Staff
🤖: ""Cloud hack alert""
Three days after Ivanti published an advisory about the high-severity vulnerability CVE-2024-8190, threat actors began to abuse the flaw.
...moreZero-Click RCE Bug in macOS Calendar Exposes iCloud Data

Published: 2024-09-17 21:26:38
Popularity: 14
Author: Nate Nelson, Contributing Writer
🤖: ""calendar crash""
A researcher bypassed the Calendar sandbox, Gatekeeper, and TCC in a chain attack that allowed for wanton theft of iCloud photos.
...moreNIST Drops Password Complexity, Mandatory Reset Rules

Published: 2024-09-26 12:30:38
Popularity: 157
Author: Edge Editors
🤖: "Password freedom"
The latest draft version of NIST's password guidelines simplifies password management best practices and eliminates those that did not promote stronger security.
...moreCritical Mozilla Firefox Zero-Day Allows Code Execution

Published: 2024-10-10 21:10:13
Popularity: 24
Author: Dark Reading Staff
🤖: ""Browser bug""
The bug is already being exploited in the wild, but Firefox has provided patches for those who may be vulnerable.
...moreInternet Archive Slowly Revives After DDoS Barrage

Published: 2024-10-17 18:26:49
Popularity: 38
Author: Kristina Beek, Associate Editor, Dark Reading
🤖: "Server recovered"
Days after facing a major breach, the site is still struggling to get fully back on its feet.
...moreCitrix Zero-Day Bug Allows Unauthenticated RCE

Published: 2024-11-13 14:03:25
Popularity: None
Author: Tara Seals, Managing Editor, News, Dark Reading
🤖: "Oh no, pwned"
The unpatched security vulnerability, which doesn't have a CVE yet, is due to an exposed Microsoft Message Queuing (MSMQ) instance and the use of the insecure BinaryFormatter.
...moreEmeraldWhale's Massive Git Breach Highlights Config Gaps

Published: 2024-11-01 21:54:23
Popularity: 12
Author: Kristina Beek, Associate Editor, Dark Reading
🤖: "Git hack alert"
The large-scale operation took advantage of open repositories, hardcoded credentials in source code, and other cloud oversights.
...moreGoogle Cloud to Enforce MFA on Accounts in 2025

Published: 2024-11-06 21:38:35
Popularity: 5
Author: Dark Reading Staff
🤖: "Secure your cloud"
Google Cloud will take a phased approach to make multifactor authentication mandatory for all users.
...moreAmazon Employee Data Compromised in MOVEit Breach

Published: 2024-11-12 22:18:29
Popularity: 11
Author: Dark Reading Staff
🤖: "Data breach alert"
The data leak was not actually due to a breach in Amazon's systems but rather that of a third-party vendor; the supply chain incident affected several other clients as well.
...more'Bad Likert Judge' Jailbreak Bypasses Guardrails of OpenAI, Other Top LLMs

Published: 2025-01-02 14:00:00
Popularity: 21
Author: Elizabeth Montalbano, Contributing Writer
🤖: ""Judge's verdict hacked""
A novel technique to stump artificial intelligence (AI) text-based systems increases the likelihood of a successful cyberattack by 60%.
...moreUnpatched Active Directory Flaw Can Crash Any Microsoft Server

Published: 2025-01-02 16:28:38
Popularity: 54
Author: Becky Bracken, Senior Editor, Dark Reading
🤖: "Server crash"
Windows servers are vulnerable to a dangerous LDAP vulnerability that could be used to crash multiple servers at once and should be patched immediately.
...more'RomCom' APT Mounts Zero-Day, Zero-Click Browser Escapes in Firefox, Tor

Published: 2024-11-26 21:36:42
Popularity: 14
Author: Nate Nelson, Contributing Writer
🤖: "Browser gets exploited"
The innocuously named Russian-sponsored cyber threat actor has combined critical and serious vulnerabilities in Windows and Firefox products in a zero-click code execution exploit.
...moreWanted: An SBOM Standard to Rule Them All

Published: 2024-07-23 23:55:56
Popularity: None
Author: Eric Braun
🤖: "Software security chaos"
A unified standard is essential for realizing the full potential of SBOMs in enhancing software supply chain security.
...moreAny IoT Device Can Be Hacked, Even Grills

Published: 2024-07-03 19:55:50
Popularity: 21
Author: Fahmida Y. Rashid, Managing Editor, Features, Dark Reading
🤖: " Grill hacked"
Researchers uncover a way to hack the summer cookout — but firmware updates will stop that grilled meat (or tofu) from turning into an inedible mess.
...moreSoftware Productivity Tools Hijacked to Deliver Infostealers

Published: 2024-07-04 13:00:00
Popularity: 11
Author: Nate Nelson, Contributing Writer
🤖: ""Info thief alert!""
Innocuous little Windows programs were carrying cheap malware for weeks, exposing customers of the India-based software vendor to data theft.
...more5 Ways to Run Security as a Meritocracy

Published: 2024-07-08 14:00:00
Popularity: 4
Author: Joshua Goldfarb
🤖: "Security badge"
Actions speak louder than words. Here are five tips for encouraging a security culture based on achievements.
...moreWill Smaller Companies Buckle Under the SEC's New Requirements?

Published: 2024-07-12 14:00:00
Popularity: 9
Author: Rob Gurzeev
🤖: "Regulatory crunch"
Even though the new incident reporting rules create pressure, they serve as a forcing function for building a strong security foundation.
...moreAT&T Breach May Also Impact Millions of Boost, Cricket, H2O Customers

Published: 2024-07-12 19:29:17
Popularity: 25
Author: Nate Nelson, Contributing Writer
🤖: "Data breach alert"
In the scrum, countless call and text records leaked, other cell companies caught strays, the DoJ became involved, and someone has already been arrested.
...moreTrusted Apps Sneak a Bug Into the UEFI Boot Process

Published: 2025-01-16 11:00:00
Popularity: 12
Author: Nate Nelson, Contributing Writer
🤖: "Uefi fail"
Seven system recovery programs contained what amounted to a backdoor for injecting any untrusted file into the system startup process.
...moreCyberattackers Hide Infostealers in YouTube Comments, Google Search Results

Published: 2025-01-13 17:26:08
Popularity: 34
Author: Elizabeth Montalbano, Contributing Writer
🤖: "Sneaky hackers"
Threat actors are targeting people searching for pirated or cracked software with fake downloaders that include infostealing malware such as Lumma and Vidar.
...moreStealthy Linux 'Auto-color' Backdoor Paints US Institutions With Malware

Published: 2025-02-26 10:18:02
Popularity: 7
Author: Elizabeth Montalbano, Contributing Writer
🤖: "Malware painting"
Attackers are using a novel malware that takes on different file names each time it's deployed; it also boasts an anti-removal mechanism to target universities and government offices.
...moreHackers Can Crack Into Car Cameras in Minutes Flat

Published: 2025-02-27 13:59:50
Popularity: 9
Author: Becky Bracken, Senior Editor, Dark Reading
🤖: ""Surveillance hacked""
It's shockingly simple to turn a car dashcam into a powerful reconnaissance tool for gathering everyday routine and location data, researchers warn.
...moreOpenSSF Sets Minimum Security Baselines for Open Source Projects

Published: 2025-02-26 23:40:14
Popularity: 4
Author: Edge Editors
🤖: "Security level up 🔒🔑"
OSPS Baseline provides a starting point for project owners and adopters to understand an open source project's security posture by outlining all the controls that have been applied.
...moreWomen Faced the Brunt of Cybersecurity Cutbacks in 2024

Published: 2025-03-06 18:35:33
Popularity: 10
Author: Kristina Beek, Associate Editor, Dark Reading
🤖: "Femme fatale hack"
Many women are finding that they are unhappy in their cybersecurity roles, largely due to the layoffs their companies are experiencing, cutbacks, and return to in-office work policies.
...moreThreat Actor 'JavaGhost' Targets AWS Environments in Phishing Scheme

Published: 2025-03-04 21:26:07
Popularity: 15
Author: Alexander Culafi, Senior News Writer, Dark Reading
🤖: "Phish alert"
Palo Alto Networks' Unit 42 details how a threat actor is dodging detection with careful targeting and the use of Amazon's native email tools.
...moreChina-Backed Hackers Backdoor US Carrier-Grade Juniper MX Routers

Published: 2025-03-12 21:14:53
Popularity: 58
Author: Rob Wright
🤖: "Backdoored routers"
Mandiant researchers found the routers of several unnamed organizations (likely telcos and ISPs) were hacked by UNC3886, and contained a custom backdoor called "TinyShell."
...moreFDA's Critical Role in Keeping Medical Devices Secure

Published: 2025-04-01 14:00:00
Popularity: 10
Author: Morey J. Haber
🤖: ""Lockdown alert""
The FDA's regulations and guidance aim to strike a balance between ensuring rigorous oversight and enabling manufacturers to act swiftly when vulnerabilities are discovered.
...moreSentinelOne Reports Services Are Back Online After Global Outage

Published: 2025-05-29 20:35:37
Popularity: 8
Author: Becky Bracken
🤖: "" Crisis averted""
The outage reportedly hit 10 commercial customer consoles for SentinelOne's Singularity platform, including Singularity Endpoint, XDR, Cloud Security, Identity, Data Lake, RemoteOps, and more.
...moreAPT41 Uses Google Calendar Events for C2

Published: 2025-05-29 20:10:15
Popularity: None
Author: Alexander Culafi, Senior News Writer, Dark Reading
🤖: "Calendar hack"
APT41, a Chinese state-sponsored threat actor also known as "Double Dragon," used Google Calendar as command-and-control infrastructure during a campaign last fall.
...moreVictoria's Secret Delays Earnings Call Due to Cyber Incident

Published: 2025-06-03 20:00:17
Popularity: None
Author: Kristina Beek, Associate Editor, Dark Reading
🤖: ""Security breach""
But that didn't stop the clothing retailer from issuing preliminary results for the first quarter of 2025.
...moreBeware of Device Code Phishing
Published: 2025-06-04 14:00:00
Popularity: 8
Author: Stu Sjouwerman
🤖: "Device hacked"
Hackers are exploiting trusted authentication flows — like Microsoft Teams and IoT logins — to trick users into handing over access tokens, bypassing MFA and slipping undetected into corporate networks.
...more1 Year Later: Lessons Learned From the CrowdStrike Outage

Published: 2025-07-02 14:00:00
Popularity: 9
Author: Nadir Izrael
🤖: "Server Down"
The ever-growing volume of vulnerabilities and threats requires organizations to remain resilient and anti-fragile — that is, to be able to proactively respond to issues and continuously improve.
...moreWe've All Been Wrong: Phishing Training Doesn't Work

Published: 2025-07-01 18:54:56
Popularity: 14
Author: Nate Nelson, Contributing Writer
🤖: "Phish Fail"
Teaching employees to detect malicious emails isn't really having an impact. What other options do organizations have?
...moreFileFix Attack Chain Enables Malicious Script Execution
Published: 2025-07-02 13:00:00
Popularity: 14
Author: Kristina Beek
🤖: ""Script injection alert""
By using social engineering tactics, threat actors are able to manipulate their victims into saving and renaming files that will backfire against them.
...moreNew 'Shade BIOS' Technique Beats Every Kind of Security
Published: 2025-08-01 13:00:00
Popularity: 16
Author: Nate Nelson, Contributing Writer
🤖: ""Bios hack""
What if malware didn't require an operating system to function? How would anyone possibly notice, let alone disable it?
...more